A story about nostalgia, freedom, and laptops…
This is part 1 of a 2-story blog. In part 2, we go even further into data and hardware isolation.
My dear laptop… choices, choices…
In 2018, I needed to replace my laptop. It was a MacBook Air, 2012 model (6.5 years of productive life), and though it probably was the best laptop I ever had, it began showing signs of age. The battery needed replacement, the disk was low on space, the RAM was limited, and its fans began spinning after about a minute or two of running. So, I started looking for a replacement. In my entire working life, I have used Windows for only two years —my preference had always been Linux. The powerful tools, the freedom, and the ability to get almost anything done were always very appealing. The only challenges at that time were that certain less technical and more “business-oriented” things were a bit tricky. Like getting external displays to work. Or connecting to certain networks. Or certain hardware. Not much of a challenge at home, where you could choose your own infrastructure, but more so in a business setting. So, when MacOS X appeared, with the combined power of a Unix kernel, nice hardware from Apple, and the usability one expects from them, I switched to a Mac. Specifically, to the PowerBook 17", and I’ve been a Mac user ever since. The natural choice for me would then be one of the new MacBook Pros — very sleek, nice hardware, etc. But something did not feel right about it.
Origin — How it started
When I started working in 1998, I implemented Netscape products for clients — the server infrastructure and client software.
 Netscape SuiteSpot software distribution CD
Netscape SuiteSpot software distribution CD
For those who did not experience those times, imagine a setting where you had to pay for an internet browser (there was really only one that actually worked) and where corporate internet sites (for those that had one) were nothing more than a glorified yellow pages entry with blue links. We were selling and implementing servers for emails and newsgroups, calendars and address books, proxying (internet connectivity was very expensive), search and crawling, certificates (PKI, LDAP), etc. This stuff was all being deployed on a flavor of Unix servers and the occasional Windows NT (often running on RISC architecture). So, from the very beginning, I had to work with the underlying infrastructure of what is today our modern internet — DNS, yellow pages, networking, routing, firewalls, services and ports, shells and scripting, processes, users, and much more. And we delivered solutions to our clients that enabled them to go to an entirely new desktop machine, fire up a browser, connect to a central server, and presto — their email, address book, calendar, network configuration, etc., were ready to use. Not bad for a business 20 years ago!
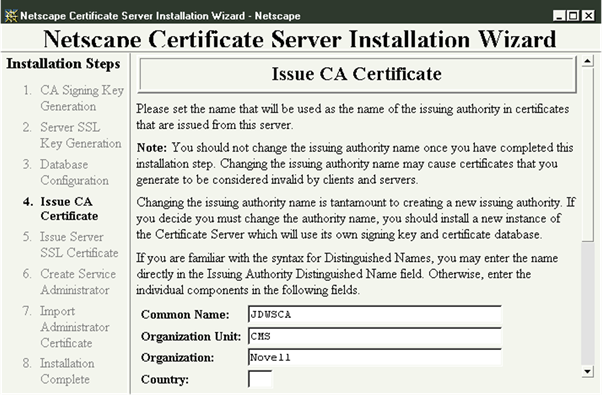 Installation admin view for Netscape Certificate Server
Installation admin view for Netscape Certificate Server
And it was all under the control of the client — using certificates for signing and encrypting mail, using LDAP as an address book, both internally and externally, setting network configuration, controlling proxies, etc. The only limitation was that there were - just like today - certain export limitations on cryptography, which meant that only US clients would get the browsers, email clients, and certificate tools that had strong encryption. Everyone else (excluding no-export countries) would get weaker cryptography. 20 years ago, this bothered me — the only reason for limiting this was to eavesdrop, but it is equally weak for everyone — malicious or benign. Well, if you aren’t doing anything illegal, you shouldn’t have to worry about this, right? To me, that is completely backwards.
Interlude — am I doing the right thing?
I recently had a client meeting together with a senior member from a big research firm, and we met again at the airport, somehow. We started talking about Marc Andreessen of Mozilla fame, and more and more things began to come together. The feeling I had about a new laptop was not so much about hardware or usability anymore. It was about getting back to my roots. I had dedicated many years to focus on open-source software, identity, and access management, but what I did and what I helped clients achieve, only went so far — it didn’t target the foundation of it all. I just don’t want anyone to have access to my information unless I explicitly allow it, whether it pertains to business situations or personal ones. There are many good reasons for this, and I will focus on one of them — the most important one for me: intent. No matter why someone has access to your information, it is simply not possible to limit what that information can be used for — due to the intent. You can limit access to the information, but once the information is out there, it can be used for anything. To me, that is the main problem. Some people tend to think that as long as someone has good intent, it is okay to give them your information (same as the “if you aren’t doing anything illegal” argument mentioned above). While I agree theoretically, in reality, you simply cannot limit the use of that information for other purposes. So, I want something that allows me to be very critical regarding who I am sharing data with. Not just clicking “I agree” on a social media site (which is consenting) but having some way to control that what I actually share is what I agreed to, and no more.
Research — what did I find?
I found an interesting company called Purism, which produces laptops. They were originally based on a crowdfunding initiative in 2015 to create a rights-respecting laptop. They raised more than 1 million USD and have since launched several updates to their product line, including a USB security key and a future rights-respecting phone. The interesting part of their products is that they focus on respecting the individual’s rights from both the software and hardware perspectives. They work with hardware that is documented, sourced in a good way, and can be powered by open-source firmware. This way, end-users can have full control over what the computer is doing and can actually inspect every single line of code used from the hardware level and upwards. Even the Intel Management Engine has been disabled, so this is about as close as we can get to respecting individual rights today.
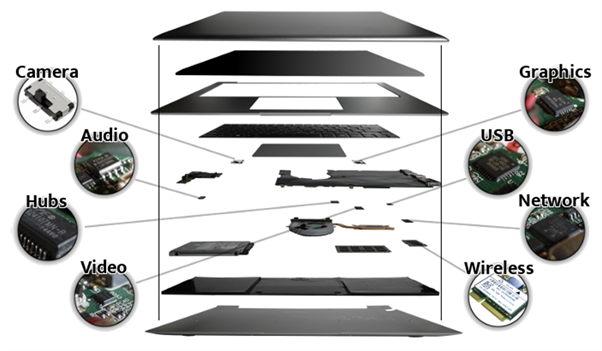 Hardware architecture of a Purism laptop
Hardware architecture of a Purism laptop
The laptop itself is a nice, black aluminium machine with features such as a TPM, physical (actually kills power) kill-switches for radio (wireless/Bluetooth), and webcam/microphone. This means that when the switch is off, it is actually physically impossible for the software to snoop on you. The laptop’s production quality is great — unlike anything I’d expect from a crowdfunded initiative. It does come at a cost though, but then again — what is your information worth?
I opted for a Librem 13 v3 and a pre-installed PureOS operating system, which is based on Debian upstream but without non-free software. After unboxing, it guided me through the initial installation and configuration, encrypted the hard drive using LUKS, and got me going in a matter of minutes. It boots using coreboot, which is a great initiative to get rid of the Intel ME and any low-level stuff. But, to be in more control, I followed the documented procedures of rebuilding coreboot, making sure (because I can) that I am booting what I think I am booting. I have now generated a key that only I know, and that can verify the boot process.
I also purchased the Librem Key, which is a USB security card produced in a partnership between Purism and Nitrokey. Basically, it is the same physical key as the Nitrokey Pro 2, relabeled as a Librem Key. This key works like a YubiKey or other similar keys, except that both the hardware and the software are open. Again — you can flash the firmware on the key with open-source software to make sure the key is doing what it should be, and not more. It can hold certificates, several credential sets (for website tech) and can support OpenPGP. I set up the key with my certificate and configured PAM on Linux (using poldi) to integrate the laptop security with the key. If I want to escalate privileges, like “sudo”, I am prompted to insert the key.
Now we are talking.
The key allows you to place your secrets on the key itself and remove all keys from the local system so that there is no way to get access without having the key (and knowing how to unlock it). This should not be done by the faint of heart, since you stand a very good chance of locking yourself out of your system permanently, if you lose your key or forget how to unlock it.
 The Purism Librem key, a Nitrokey partnership
The Purism Librem key, a Nitrokey partnership
The LUKS disk encryption (I have two encrypted drives in the Librem 13) can also work with the key to decrypt when the key is present/unlocked and encrypt when the key is removed/locked. I have this set up and working, but I will get some backup keys before I default to this behaviour.
Hold your horses!
But, hang on a minute, isn’t all this stuff also available if you buy a YubiKey, run secureboot, use the new T2 chip on Apple machines, etc.? Well, most of it, yes. But then you would be trusting Intel, Apple, Microsoft, and others — they might be increasingly focusing on security, but definitely not on freedom. If that is okay with you, fine. Just beware; you might not be able to fix or upgrade your machine by yourself, or source the parts you want. You might not be allowed to run the software or operating system you want on that particular hardware. You could be locked out of your own system just by doing the things you want with it. And you are susceptible to a whole bunch of security issues that you can do absolutely nothing about. That, definitely, is not for me.
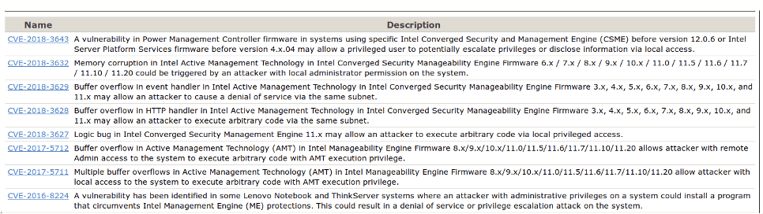 Example registered vulnerabilities related to Intel ME
Example registered vulnerabilities related to Intel ME
These are not trivial vulnerabilities and they are introduced by something I (the end-user) am not really interested in.
Deeper down the rabbit hole…
The next thing I am working on, is on getting Heads (http://osresearch.net/Installing-Heads) to work with the key. Heads is a solution for having a tamper-free BIOS boot process, where it uses the Trusted Platform Module (TPM) on the laptop and prompts for a one-time code. This one-time code can be generated by Google Authenticator or similar, or it can use the Librem Key.
Currently, this is an approach that can be used only for specific hardware, and in many cases, you need to access and tamper with the physical hardware to get access.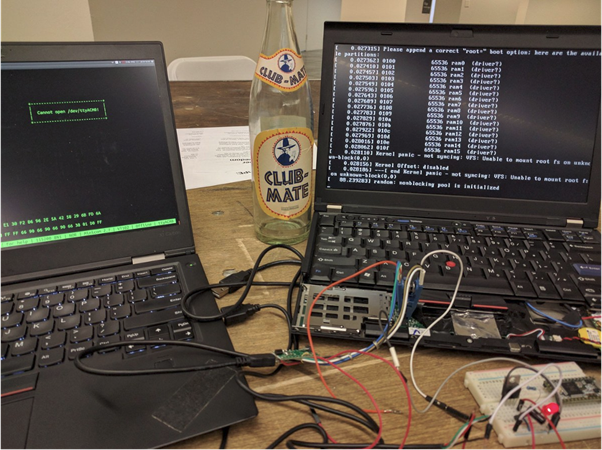
Picture from osresearch.net
However, for the Librem laptops, this is not necessary, as the hardware and firmware are all open. Yeah!
Heads can be set to stop the boot process if you don’t have the right code or just to warn you when someone has tampered with the laptop. I am setting the laptop up so that the green LED on the key lights up when the code matches, and the red LED lights up when it doesn’t. Very cool stuff!
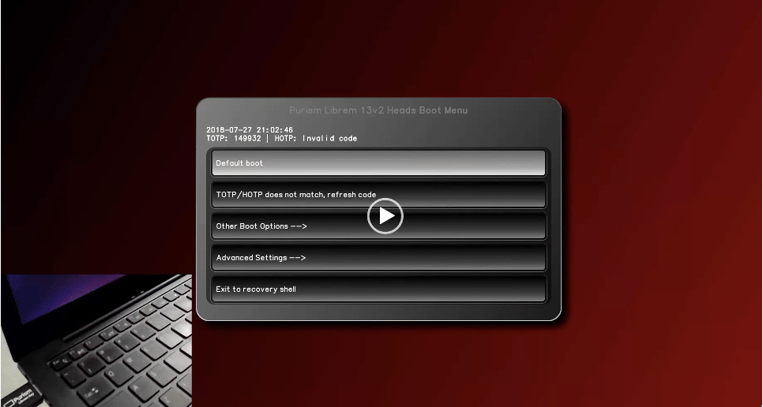 Boot picture when code is invalid
Boot picture when code is invalid
So now I have a laptop which can follow a strict security policy: boot security, encrypted disks, multi-factor authentication where I want it, and the ability to completely remove security credentials from the computer, by storing them only on the security key.
Finally, I have found something that makes me feel good about my choice! So, the next time you think of buying a new laptop or phone, do consider putting pressure on vendors about your rights. Is the laptop truly yours? Can you do what you want with it? Can you restrict access to your information and verify that what is shared is _only_ what you agreed to?
In any case, please do consider that your hardware (and software) is eavesdropping on you, sharing information with parties you do not know about, and restricting how you can use your own (!) machine. And those same mechanisms have vulnerabilities that are exploited by agents with all kinds of agendas. The Librem is not a computer for everyone, but I hope this post makes everyone understand that it is important that hardware and software respects our rights as consumers and that the trade-offs that are made actually do just what they said they would, and no more.
After all, it isn’t paranoia if you are actually being followed, right?
Onwards!
Please note: the author and his employer have no affiliation with Purism Inc.
Originally published here.





